10 Essential Tips for Using Custom Containers Effectively
Custom containers have revolutionized how we deploy applications. They provide an isolated environment that ensures consistency across different systems. However, using custom containers effectively is not always straightforward. Many newcomers struggle with various aspects of container management, leading to common pitfalls.
Understanding the nuances of custom containers can significantly enhance productivity. Tweaking configuration settings might seem trivial, yet these adjustments can make or break the deployment process. Without proper knowledge, users might end up with containers that are too large or inefficient. This is a frequent oversight, creating unnecessary complexity.
Incorporating best practices is essential to leverage the full potential of custom containers. For example, using a minimal base image can reduce the overall size and improve performance. Additionally, it is vital to keep security concerns in mind while managing containers. Overlooking these details can result in vulnerabilities. By reflecting on these challenges, one can improve their strategies for using custom containers effectively.

Understanding the Benefits of Custom Containers in Software Development

Custom containers have revolutionized software development. They allow for isolated environments, ensuring applications run smoothly. This is crucial, especially in complex systems. Developers can package apps with dependencies, enhancing portability and reducing conflicts. As teams embrace custom containers, understanding their benefits becomes essential.
One key tip is to prioritize security. Custom containers can introduce vulnerabilities if not managed correctly. Regularly update container images. Monitor for any security patches. This vigilance prevents potential breaches. Another valuable tip is to optimize container size. Smaller containers are faster to download and deploy. This can lead to efficient resource usage. Less memory and CPU are needed, which improves overall performance.
Customization is also a double-edged sword. While tailoring containers to specific needs can boost efficiency, it may complicate maintenance. Document your configurations clearly. Without proper documentation, teams may face challenges when troubleshooting or scaling solutions. Embrace the power of custom containers but remain aware of the potential pitfalls that could arise. Adjust strategies as you learn from each experience.
Key Factors for Choosing the Right Container Runtime for Your Needs
Choosing the right container runtime is crucial for efficient application deployment. It directly impacts performance, security, and resource utilization. Not every runtime suits every workload. You need to analyze your specific requirements carefully before making a decision.
Consider the compatibility of the container runtime with your existing infrastructure. Check if it supports the orchestration tools you plan to use. The right integration can simplify management and improve scalability. If the runtime lacks community support, addressing issues can become challenging. This can affect your deployment timelines.
Evaluate the security features of the container runtime. Some offer advanced isolation methods. This can safeguard your applications from vulnerabilities. However, more features don’t always mean better security. Ensure that you understand the trade-offs involved. Test different configurations to find the sweet spot for your unique environment.
10 Essential Tips for Using Custom Containers Effectively
Best Practices for Optimizing Performance of Custom Containers
When working with custom containers, performance optimization is crucial. Start by choosing the right base image. Choose one that is lightweight yet functional. This can greatly reduce startup time and memory consumption. Use only the necessary components for your application. Unused packages can bloat your container, impacting performance negatively.
Efficient resource allocation is another key aspect. Allocate CPU and memory limits carefully. Insufficient resources can slow down your application, while excessive allocation can waste valuable infrastructure. Monitor your container's performance metrics regularly. This helps identify bottlenecks or inefficient processes that need addressing. Remember, not all configurations will be perfect on the first try. Be ready to iterate and refine your setup.
Consider scaling strategies as well. Sometimes, multiple smaller containers can outperform a single, larger one. Test various configurations to find the best fit for your needs. Be mindful, though. Every environment is different, and what works well in one case may fall short in another. Always have room for adjustments as you learn more about your workload characteristics.
Strategies for Managing Container Security in Production Environments
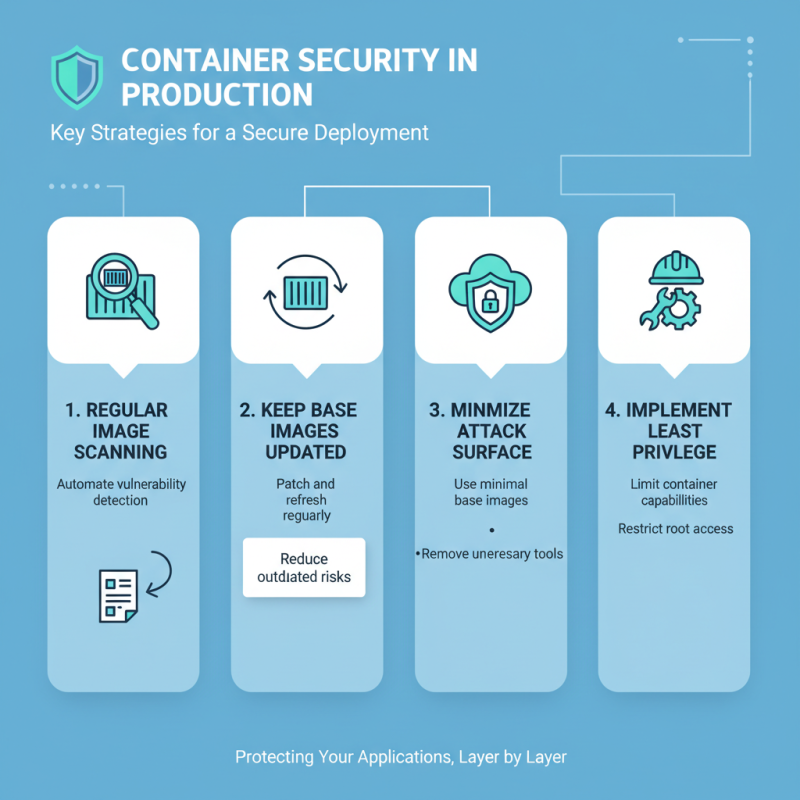
Managing container security in production environments is critical. Containers can introduce vulnerabilities if not secured properly. One effective strategy is to regularly scan images for known vulnerabilities. This includes using automated tools that can identify and report issues promptly. It's important to keep your base images up to date. Using outdated images can create significant security gaps.
Another vital strategy is to implement role-based access control. Limiting access reduces potential risks significantly. Ensure that only authorized personnel can interact with containers and their orchestration tools. Logging and monitoring are equally essential. Utilizing logging tools helps in tracking unusual activities. These insights can reveal potential security breaches early.
Using secrets management tools can also enhance container security. Storing sensitive data securely minimizes exposure. However, many teams overlook this step, leading to unexpected risks. Regularly review your security policies and practices. Reflect on incidents that may have occurred. Adjust your approach based on lessons learned. This continual improvement loop helps in staying a step ahead of potential threats.
Monitoring and Logging: Essential Tools for Custom Container Management
Monitoring and logging are critical to managing custom containers effectively. According to a 2022 report by the Cloud Native Computing Foundation, 75% of organizations struggle with monitoring their containerized applications. Without proper tools, visibility into operations diminishes. Inefficient logging can lead to overlooking crucial performance metrics. Consequently, teams often miss out on essential insights.
Utilizing efficient monitoring solutions is vital. They should support real-time data analysis. A survey from Grafana Labs revealed that 60% of users face challenges integrating logs and metrics. This integration is key to understanding application behavior. Failing to correlate these data points can result in delayed incident response times. In many cases, teams remain unaware of underlying issues until they escalate.
Logs serve as a breadcrumb trail. They help in tracing back issues when things go wrong. According to research by Dynatrace, 40% of incidents aren't resolved on the first attempt due to poor log management. This inefficiency can drain resources and hinder team productivity. Focus on refining your logging strategy is essential for continuous improvement.
10 Essential Tips for Using Custom Containers Effectively - Monitoring and Logging: Essential Tools for Custom Container Management
| Tip Number | Tip Description | Tool/Platform | Key Features |
|---|---|---|---|
| 1 | Implement Consistent Logging Practices | Fluentd | Unified logging layer, support for various data sources, real-time log processing |
| 2 | Monitor Resource Utilization | Prometheus | Time-series data collection, powerful queries, alerting capabilities |
| 3 | Ensure Container Security | Aqua Security | Vulnerability scanning, runtime protection, compliance checks |
| 4 | Optimize Network Performance | Weave Net | Easy multi-host networking, encryption, network traffic visualization |
| 5 | Set Up Alerts for Critical Metrics | Grafana | Data visualization, alerting, support for multiple data sources |
| 6 | Use Centralized Logging | ELK Stack | Log storage, search capabilities, data visualization |
| 7 | Implement Health Checks | Kubernetes | Automatic health checks, rolling updates, scaling |
| 8 | Keep Images Lightweight | Docker | Layer caching, quick deployment, reduced overhead |
| 9 | Implement Asynchronous Processing | RabbitMQ | Message queueing, flexible routing, reliability |
| 10 | Regularly Review and Update Configurations | Ansible | Configuration management, automation, idempotency |
Related Posts
-

Unlocking the Potential: Innovative Uses for Specialty Shipping Containers in Modern Industries
-

Exploring the Versatility of Custom Cargo Containers: Innovative Uses for Modern Transport Needs
-

Unlocking the Potential of Custom Built Shipping Containers for Sustainable Living Solutions
-

Top 5 Converted Container Designs Transforming Modern Living in 2025
-

Top Construction Container Trends to Watch in 2025 for Your Next Project
-

Top Benefits of Using Construction Containers for Your Building Projects

